From the WannaCry ransomware storm of 2017 to the infamous SolarWinds hack of 2019, to 2023’s MailChimp hack, cyber risk is a concern for every company. Multinationals and small and medium enterprises alike are now equally likely to suffer from phishing, code injection attacks, insider threats, and DNS tunneling.
The good news is that as cyber threats grow, CEOs are increasingly emphasizing building resilience to minimize business disruption while prioritizing strategic cyber risk management.
In the past, many companies have purchased a variety of cybersecurity tools to solve specific threat problems but lack a comprehensive cybersecurity strategy. Today, they are looking to scale and mature their existing frameworks and identify gaps in their practices. In this process, many companies have realized they lacked the in-house cybersecurity expertise and maturity to develop comprehensive cybersecurity programs, or to create future-state assessment roadmaps.
Today, companies also need to think about defence mechanisms for both in-office and remote workers, while ensuring stringent compliance with cybersecurity standards.
Many of these companies are seeking third-party expertise to help build new end-to-end application security services and future-state maturity assessment roadmaps. Others are looking for cybersecurity partners to review and enhance their existing threat management audit programs and help improve effectiveness by complementing their teams with critical skillsets. This includes identifying new and emerging risks such as open-source software, software bill of materials, the internet of things, and supply chain issues. Many are also looking for help on how to remediate and report against vulnerabilities, or simply recommendations on new tools, configurations, or capabilities.
This white paper will demonstrate how EXL can help companies to mature their cyber security programs through an end-to-end approach, including our expertise in building, diagnosing, and designing. Using case study examples, the white paper will show how our audit and assessment services are helping multinational organizations to understand their gaps and issues, and how our highly skilled global teams are helping companies to achieve better operational resilience.
Our approach to the cybersecurity services value chain
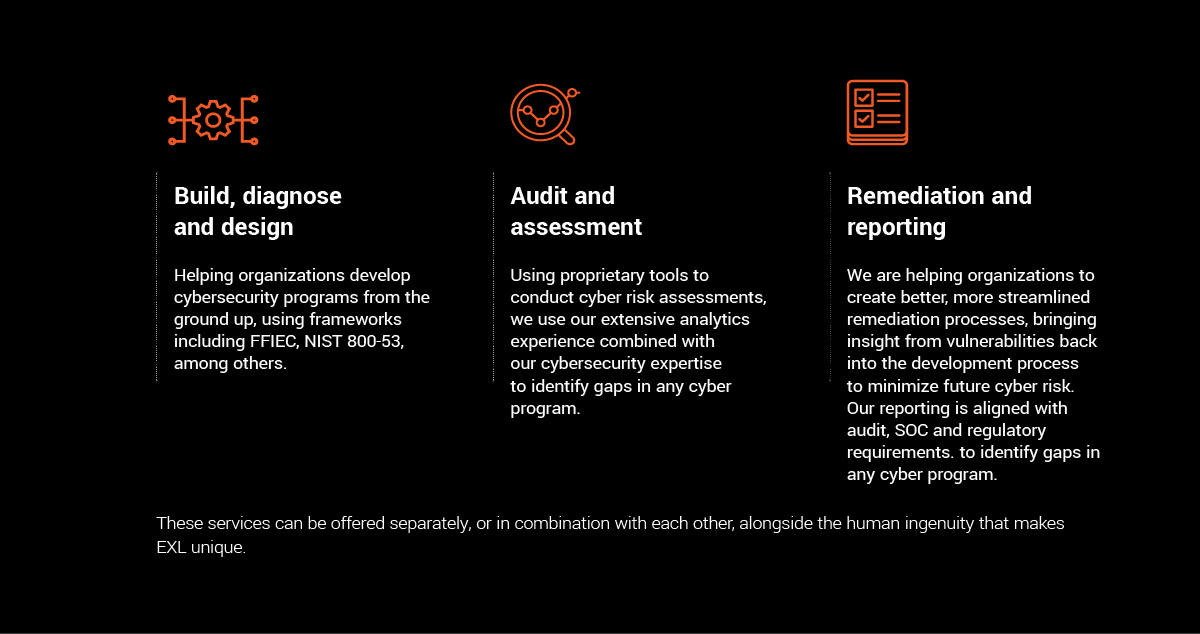
As part of our end-to-end application security services, EXL offers three core focus areas including:
We provide an end-to-end approach that includes risk analysis and threat modelling, a protective technology review, threat identification and mitigation, and incident management, response, and recovery.
Build, Diagnose and Design: Robust, mature, end-to-end cyber programs
In the build and design phase, there are common goals in achieving top threat coverage and compliance. Every company wants to prepare against and detect breaches before they happen by covering all organizational systems. Today, companies also need to think about defence mechanisms for both in-office and remote workers, while ensuring stringent compliance with cybersecurity standards.
However, beyond these common goals, there is no one-size-fits-all framework when it comes to implementing, maintaining, and scaling end-to-end application security services. Each industry and vertical faces different challenges, while also dealing with its own product-specific frameworks for cybersecurity. While banking may be more focused on how the Federal Reserve Board will treat risks, healthcare is more often focused on FDA and HIPAA compliance. Every industry is unique in the risk management capabilities it requires, and a successful approach to threat and risk requires that cybersecurity and domain expertise is carefully mapped against these requirements as well as to ensure that it addresses the risks which are unique to every business.
Domain expertise-driven design and build sits at the heart of the cybersecurity services value chain. EXL is focused on helping our customers to diagnose their problems, measuring their cybersecurity and application security program maturing using industry. EXL can develop cybersecurity programs from the ground up using frameworks like FFIEC, NIST 800-53, among others.
We also offer competitive differentiation through lower cost: EXL’s network of well-established global delivery centers enable our customers to leverage the scale we’ve already built. The benefit of this is that our customers don’t have to pick and choose critical applications to focus on due to budget constraints. Instead, they get a full, end-to-end assessment and cyber security offering.
Audit and assessment: detecting vulnerabilities in the cyber landscape
As Gartner explained in its Top Priorities for Audit Leaders in 2023, chief audit executives have identified a range of cybersecurity and technology-related risks as top coverage priorities for 2023. However, less than 30% of CAEs are confident in providing assurance over ransomware and state-sponsored cyberattacks1.
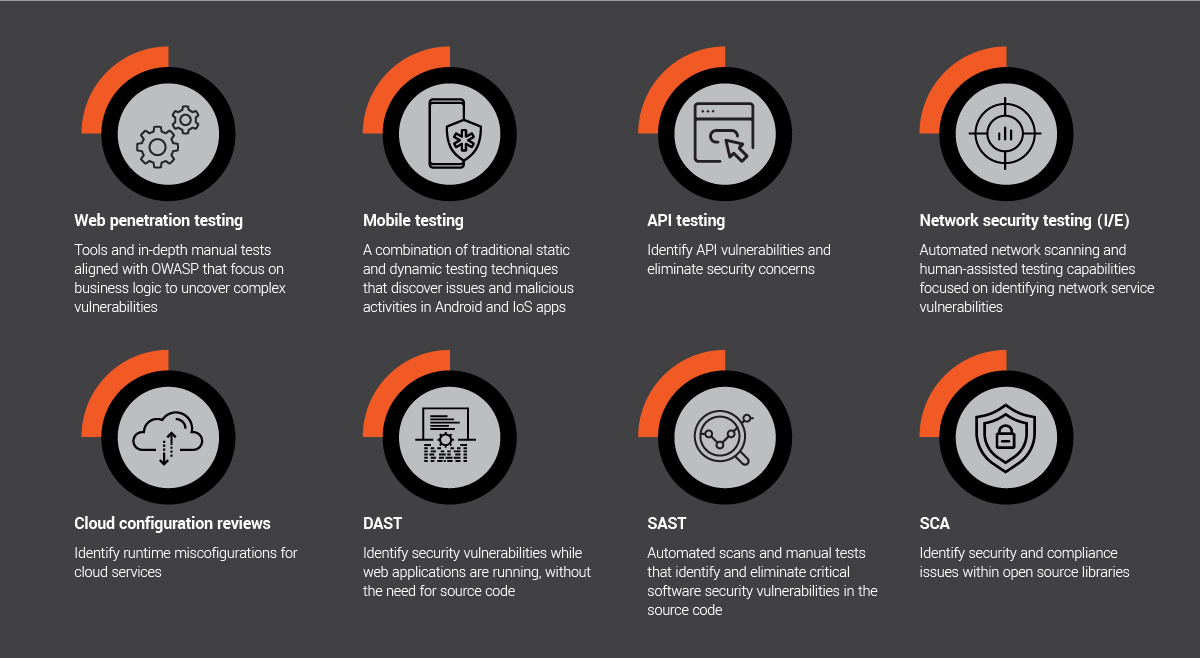
This is why EXL’s cybersecurity risk services focus on helping companies with assessments and audits to identify gaps in their practices. While all companies will run assessments quarterly or twice yearly, EXL can help companies to streamline these assessments. Our assessment and audit services are helping companies to identify gaps, and to mature their cyber security programs. We provide an end-to-end approach that includes risk analysis and threat modelling, a protective technology review, threat identification and mitigation, and incident management, response, and recovery.
We have unparalleled expertise using proprietary tools to conduct cyber risk assessment, as well as extensive compliance experience in CCPA, GDPR, PCI, HIPAA, FERPA, SOC 1 & SOC 2, ISP 270001, ISO 27017, and others. We provide cyber risk assessments that identify sensitive data in any file format automatically, allowing you to classify it, secure it, and easily monitor it any time it is accessed.
A snapshot audit and assessment case study: EXL improves cyber threat management for a leading pharmaceutical and consumer products organization
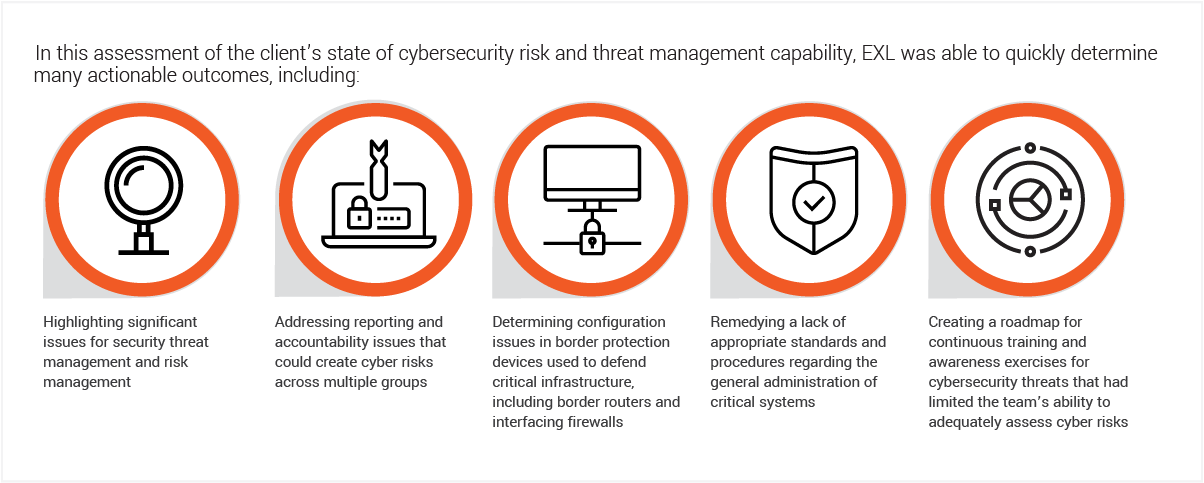
In 2022, a large healthcare company engaged EXL to assess its current state of cybersecurity risk and threat management capability, as well as gaps in its cybersecurity practices. The company was looking for a cybersecurity partner to review and enhance the existing threat management audit program to help improve effectiveness of the audit program while identifying new and emerging risks.
The healthcare company had originally used a third party to run its security operations center, limiting transparency and insights surrounding cyber threat behaviour and management. Its lack of in-house cybersecurity domain and compliance expertise had prevented an effective evaluation of any existing gaps in its cyber security practices, as well as ongoing cyber risk assessment.
Outcomes
1 Audit Top Priorities (gartner.com)
Remediation and reporting: Building intelligence on vulnerabilities
Despite all efforts, breaches do happen on occasion. However, the way a business handles these events is critical in building a mature, robust cyber program. Strong remediation in cyber security means addressing the breach proactively and limiting the amount of damage it can potentially cause to your business and your people.
Forrester predicted that in 2023, some global firms will be exposed for burning out their cybersecurity employees. When a breach occurs, the exposure can impact a huge array of data in the form of millions of records or customer accounts. Breaches can also expose misconfigurations and poor development practices, which can be extremely time-consuming to fix.
To retain talent and empower cybersecurity employees, EXL helps companies with remediation and reporting abilities that align with audit program security office centers (SOC) and any regulatory requirements.
We differentiate by bringing vulnerabilities back into our training of cybersecurity teams. Using our assessment capabilities, we can determine where the vulnerabilities lie. For example, if there are vulnerabilities in input validation or cross-site scripting, developers need to learn to write code that is not susceptible to input validations - or to put enough controls in place that any input validations or hacking techniques cannot be utilized to infiltrate the system.
Effective remediation must be about bringing in the learnings and insights generated from experiencing vulnerabilities. EXL’s analytics expertise contributes to generating insight surrounding vulnerabilities, inputting this information into the development community to improve security throughout the entire software development lifecycle.
Remediation should also work to help cyber security employees and to prevent burnout. According to the most recent (ISC)2Cybersecurity Workforce Study, 47% of cybersecurity professionals have experienced burnout or stress during the past year. However, there are practices that can help. For example, we triage and categorize vulnerabilities to identify false positives so that it becomes easier for SOC analysts to review threat alerts. We also design persona-based dashboards customized to different stakeholders, from those on audit committee and boards, to CISOs and analysts.
What sets EXL apart?
EXL has been a trusted partner to many Fortune 500 organizations for over 20 years, employing over 6,900 data scientists and engineers across more than 800 companies around the world.
With the cyber threat landscape expanding and changing so rapidly, even large organizations may struggle to keep on top of threats, or to hire the in-house cybersecurity talent required to stay ahead of attackers. Our team’s extensive experience in using proprietary cybersecurity tools is unparalleled, and our assessments are helping companies to identify the gaps that lead to data breaches and attacks. As companies face increasing disruptions and escalating costs associated with cyber threats, we are helping to build and scale mature, robust cyber programs to reduce vulnerability and increase resilience.